Beihang classified confidential research network
Beihang's confidential research network undertakes important national scientific research tasks, and the confidentiality level is designed according to the confidentiality level. Starting from the actual situation of Beihang University, the system requires scientifically formulating a comprehensive plan that is safe, practical, reliable, efficient, and scalable to meet the needs of scientific research to the greatest extent, improve work efficiency and scientific research level; ensure information security and smooth network become the success or failure of project implementation key.
This project includes: integrated wiring, network and security, server, storage, network security and other parts.
All the integrated wiring adopts Nexans six-type shielded wiring system, which is designed and constructed in strict accordance with the requirements of the national dense network. More than 20 Class C shielded cabinets were selected to build a dedicated grounding and lightning protection system. Equipped with Merlin Rilan 60KVA UPS power supply.
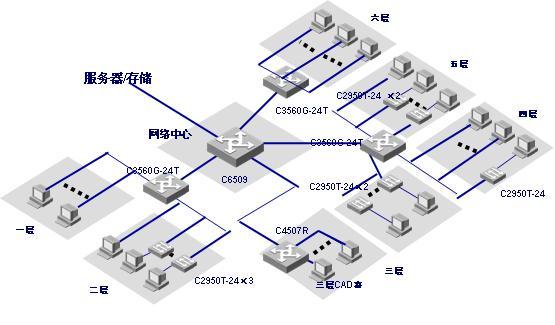
The core layer of the network uses CISCO 6509 10 Gigabit core switches, and the aggregation layer selects CISCO 4507R and 3560 switches, and Gigabit switches to the desktop. See the network diagram below:
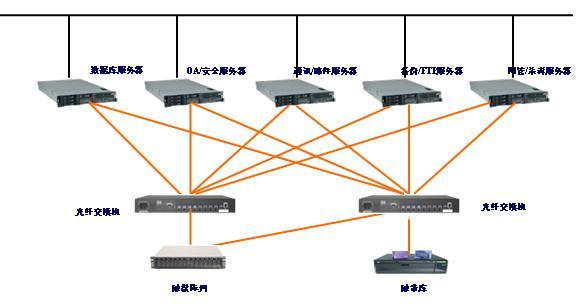
Equipped with IBM eServer® xSeries® 365 rack-optimized 5 servers with 4-way processors, STK's disk array FLX240 storage system, StorageTek L20 tape library and LEGATO network backup system regularly back up the system.
Select the Rongji Security Vulnerability Scanning System: regularly scan and evaluate the overall security situation of the intranet, provide expert-level correction suggestions, and take precautions. Use Kaspersky online version of anti-virus software to kill viruses; select Kaspersky online version of anti-virus software to kill viruses; select HP OPENVIEW to manage network devices, servers, computers, etc .; choose video information password jammer to solve the protection of computer electromagnetic radiation information leakage problem.
Select a network security protection system to protect the entire process of storage, dissemination, processing and destruction of computer sensitive information, and conduct comprehensive monitoring and auditing of comprehensive security and confidentiality protection products for confidential networks and computers. It consists of four subsystems: host monitoring and auditing system, terminal security and file protection system, secret computer online monitoring and forensics system, and network vulnerability forensics system. The four subsystems work together to protect the user's network, terminal computers, and confidential information in all directions.
Two pieces of black base and clear lid rectangular bento box are available are available in a variety size options. Aside from sushi try these for light weight deli, snack or appetizer presentations too. Precision process and exacting details pursuit of perform can show your food in good display.
Rectangular Disposable Lunch Box
Rectangular Disposable Lunch Box,Rectangular Disposable Bento Box,Disposable Black Lunch Box,Plastic Lunch Box With Lid
Taishan MeiBao Plastic Products Co.,Ltd , https://www.meibaoplastic.com
![<?echo $_SERVER['SERVER_NAME'];?>](/template/twentyseventeen/skin/images/header.jpg)